Aws client vpn endpoint. AWS Client VPN now includes support for AWS CloudFormation 2020-01-20
Getting Started with Client VPN

Compatibility with your employees' devices. How can I make this change? I was able to monitor my client connections as they were happening. To grant access to all users, for For grant access to, choose Allow access to all users. Step 1: Generate Server and Client Certificates and Keys This tutorial uses mutual authentication. Now I just need to download the client configuration from the console. I used private subnet for this. Edit it with your favourite editor and add the following lines to the bottom: cert.
Next
Access to a VPC
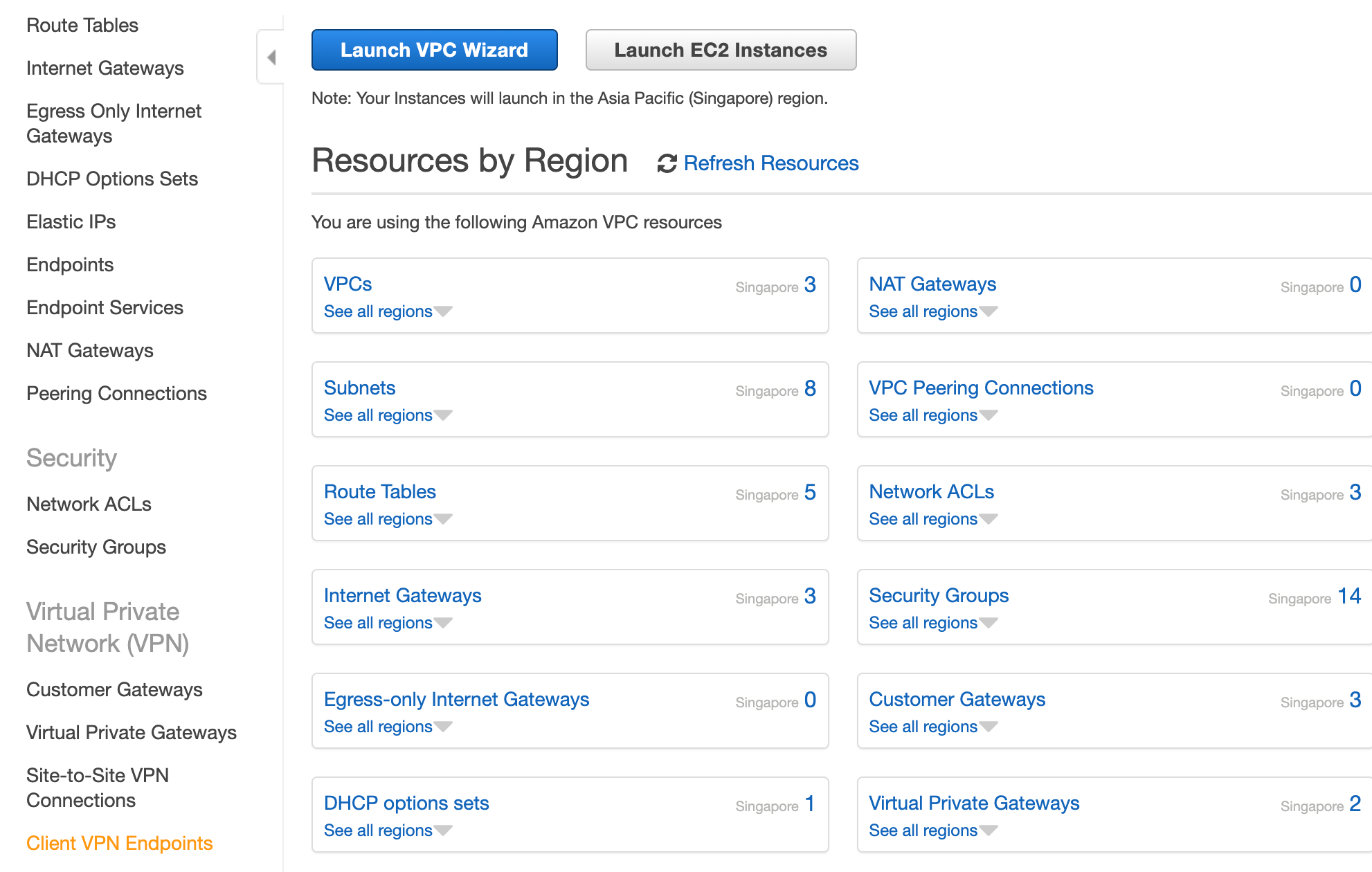
A: Yes, you can specify if you want split tunnel during the creation of the endpoint or modify the endpoint configuration to enable split tunnel. This way it will allow public instances to communicate publicly. . Billing is pro-rated for the hour. If that port is not open the tunnel will not establish. Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
Next
aws_ec2_client_vpn_endpoint timeout is too low · Issue #7871 · terraform

The only way we managed to get around it, is to delete the stack and start again. Q: Do your prices include taxes? Do you want to log the details on client connections? From there, I select Apply Security Groups. Some of the solutions inject add into webpages you visit. A: You configure authorization rules which limit the users who can access a network. You may need to tab in and out to see the change.
Next
AWS VPN pricing
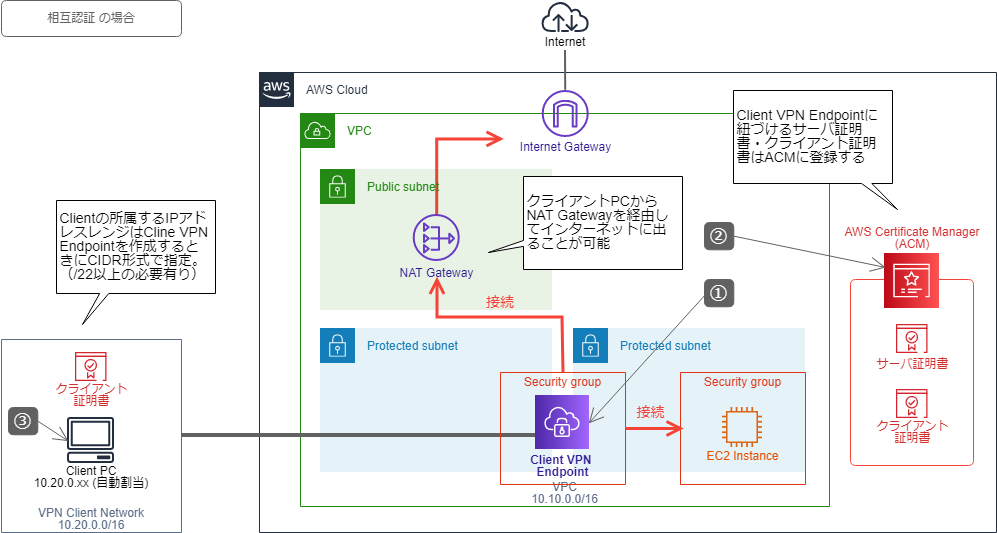
It is elastic, and automatically scales to meet your demand. Once done all states should be green. Would that block their ability to communicate to the outside world, e. The connection logs include details on created and terminated connection records. Pre-shared keys are the default method, where a string key is used for authentication. Download the Client Configuration Now that we have our infrastructure provisioned and configured, out final step is to download the client configuration.
Next
aws_ec2_client_vpn_endpoint timeout is too low · Issue #7871 · terraform

Q: How does the split tunnel work? I was determinted to give it a try. Generate Certificate and Keys You need to generate certificate and keys for servers to process client vpn first. Issue one is that the endpoint can not be trusted the provider might be capturing all user traffic for a number of reasons. Q: What is a target network? This is key for spiky workloads, such as the typical ebbs and flows of workforce connectivity throughout the day. There you are presented with a form to fill out. For each additional network, you must add a route to the network and configure an authorization rule to give clients access.
Next
AWS: aws_ec2_client_vpn_endpoint

Capitalized terms used herein but not defined herein shall have the meanings set forth in the Agreement. You can also manage active client connections, with the ability to terminate active client connections. You can leave the stream name field empty. Billing is pro-rated for the hour. Q: I use CloudHub today. Q: What is the cost of using a virtual private gateway? For this walk-though we are only showing Active Directory authentication.
Next
Introducing AWS Client VPN to Securely Access AWS and On

The script that is being used can be found on if you want to review it or fork it. A: You can choose the method of authentication based on your security or compliance needs. Once created, wait for a ew minutes till Directory service is ready. The main difference between private and public subnet is whether an internet gateway is employed. If you have your own tables defined, you can delete this and apply by other means. Split tunnel is not enabled by default. But am not able to connect or ping to the ec2 instance from my local instance.
Next
AWS VPN features
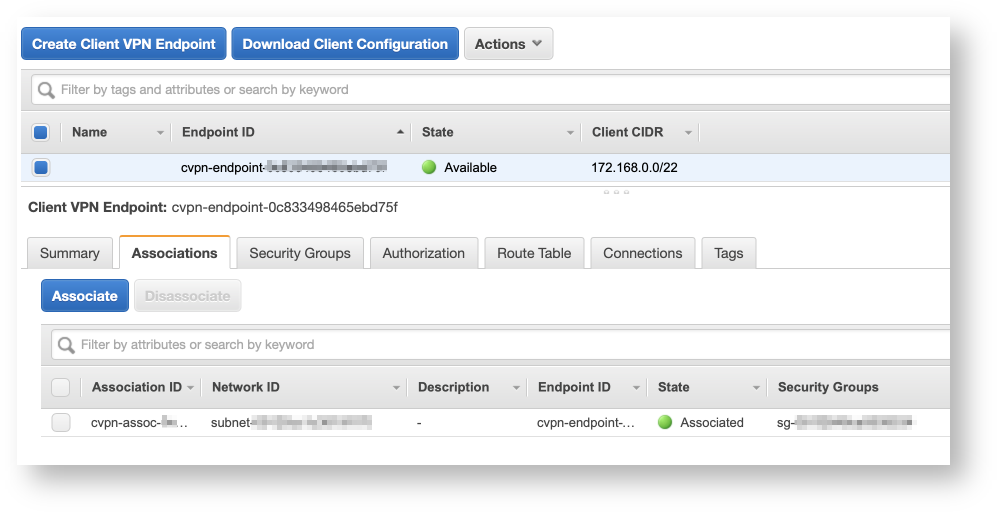
In this tutorial, we add a route to the internet 0. So yes, that should be possible. For a specified network, you configure the Active Directory group that is allowed access. Which was interesting because no one had seen a blog or any release information about it. Also is there value in hosting production servers in a private subnet vs the default public one? I have previously deployed a managed Active Directory, so I will choose that. How can I make this change? Q: Can I monitor by endpoint using CloudWatch? I maintain and update this blog in my spare time.
Next
AWS VPN pricing

You can setup only one Active Directory server for authentication. Simple apply the file to whatever client you are using, typically via a double-click or drag-and-drop. Choose the appropriate installer version for your version of Windows. Q: Which Diffie-Hellman groups do you support? Radio Button If Yes, sets up a CloudWatch log group and stream. Please ensure that your time and date are correct on this system.
Next







