Cidr notation. What is CIDR (Classless Inter 2019-12-29
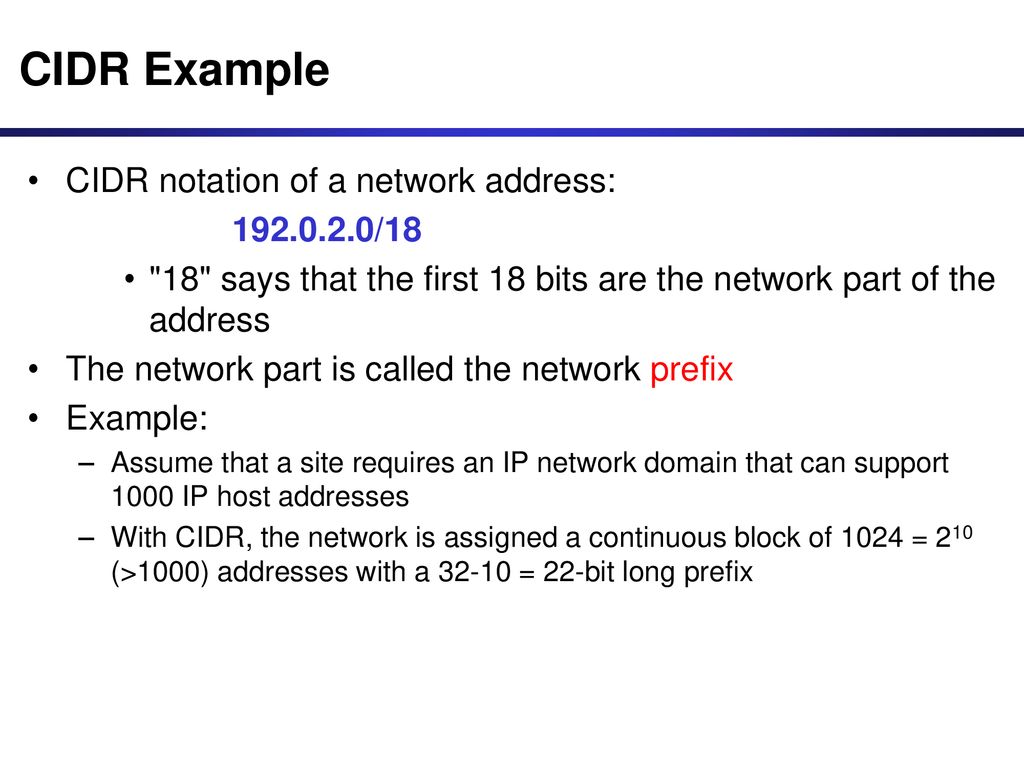
What is CIDR notation?
For example, a class A network could accommodate over 16 million hosts, but only 128 0-127 of these networks were available. And the longest sequence of zeros as '::'. See Examples 1, 2, 3 above. End { } End End. Class A addresses used the remainder of the first octet to represent the network and the rest of the address to define hosts. .
Next
RFC 4632
If you want to understand this in detail, it makes sense to look at a subnet mask in its binary form: 255. . As a recap, it works this way. . Security Considerations The introduction of routing protocols that support classless prefixes and a move to a forwarding model that mandates that more-specific longest-match routes be preferred when they overlap with routes to less-specific prefixes introduces at least two security concerns: 1.
Next
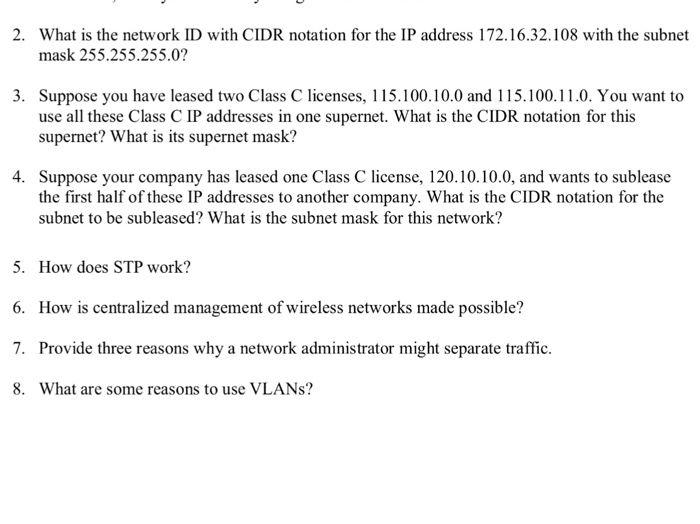
1.5. Understanding CIDR Subnet Mask Notation

Consider the example of broadcasts — every host within an individual network will receive a broadcast even when it is not meant for them. An organization that needed more than 254 host machines would often get a Class B license, even though it would have far fewer than 65,534 hosts. The reason for this can be seen when both addresses and the corresponding subnet mask are represented as binary numbers. . . The aggregation of multiple contiguous prefixes resulted in in the larger Internet, which whenever possible are advertised as aggregates, thus reducing the number of entries in the global routing table.
Next
Understanding IP Addresses, Subnets, and CIDR Notation for Networking
Similarly, there is no hard requirement that any end site renumber when changing transit service provider, but end sites are encouraged do so to eliminate the need for explicit advertisement of their prefixes into the global routing system. We can use those borrowed bits to create additional networks, resulting in smaller-sized networks. This means that several addresses are combined into one route. Instead, any power of 2 can be used as a size of the network number of hosts + network address + broadcast address. To illustrate the problems with the class system, consider that one of the most commonly used classes was Class B. .
Next
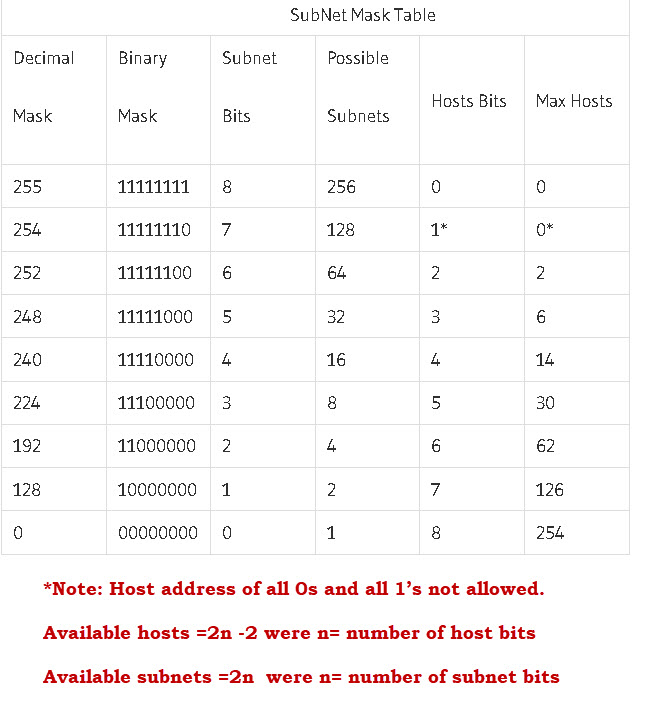
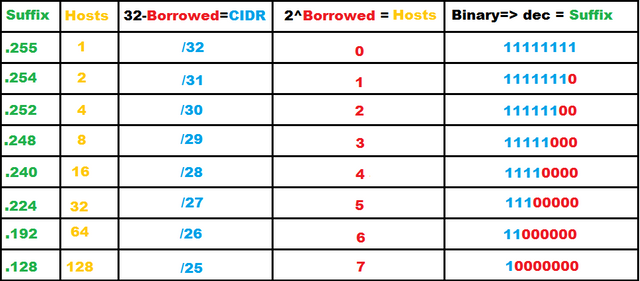
CIDR Subnet Mask Cheat Sheet
This is explained in and supported by many vendors including Cisco. Therefore, instead of having for example 16-bits on the network part by using the old Class B assignment you can have for example 20-bits on the network part and thus 12-bits of the remaining length for the host part. . Responsibility for and Configuration of Aggregation. And how does the internet protocol actually work? Binary computational operations and long series of numbers are frightening, but the principle itself is not so complicated. . .
Next
What is CIDR (Classless Inter

. . This block is described by the route 10. . .
Next
Online IP CIDR / VLSM Supernet Calculator

. Assuming that the best common practice for network administrators is to exchange lists of prefixes to accept from each other, configuration of aggregation information does not introduce significant additional administrative overhead. . . There are various calculators and tools online that will help you understand some of these concepts and get the correct addresses and ranges that you need by typing in certain information. Dig Deeper on Network protocols and standards I found this explaination to be terribly confusing and ambiguous. Another reason is that many people have not had enough practice with subnetting.
Next
Introduction to Subnetting
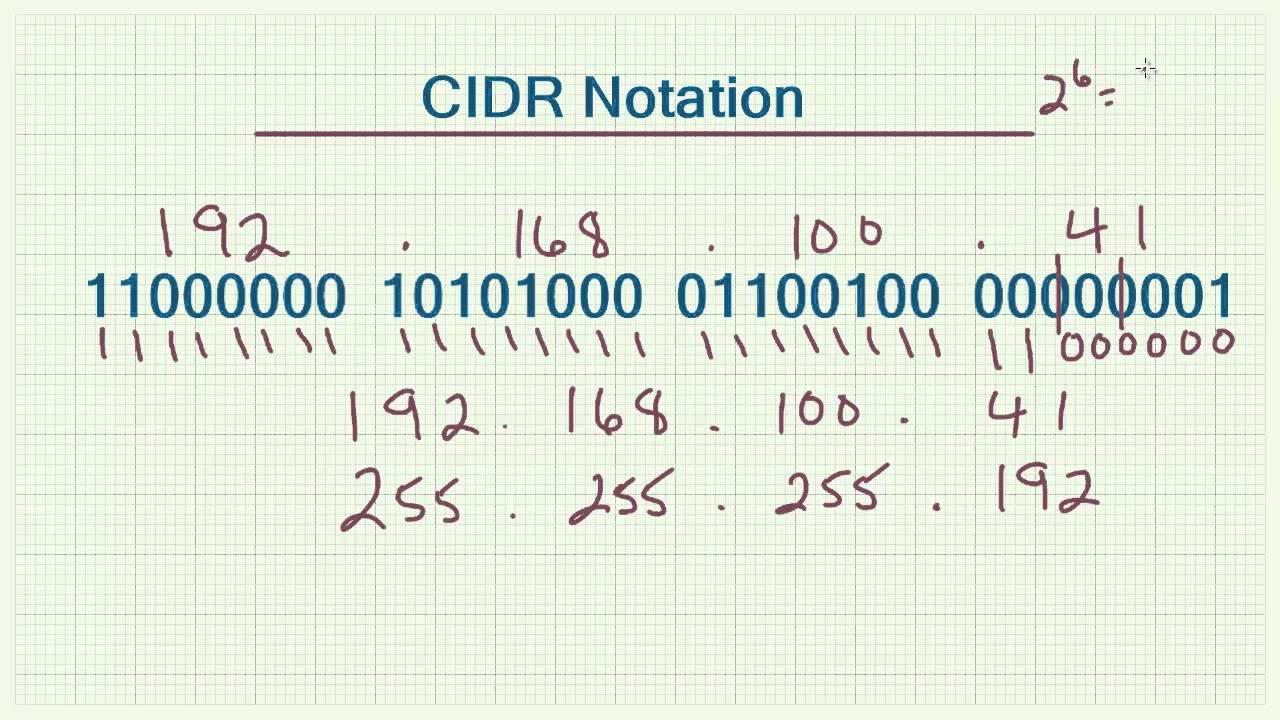
We add 1 because the first address is the network address and we subtract 2 instead of 1 because the last address in a subnet is the broadcast address. . To kick off the next season, Anthony met with Lacy Surber during the 250ok and MailerQ Global Sender Summit in Amsterdam. The below examples display a few results, but eventually return all the possible results. These aggregate routes are advertised into the global routing system by the border routers for the routing domain.
Next
What is CIDR (Classless Inter

. Netmasks and Subnets The process of dividing a network into smaller network sections is called subnetting. It would make sense — also in the sense of the routing table — to turn it into a supernet. Networks The bits in the 'host' part of a network address are all '0'. . This is reason enough to learn more about class inter-domain routing. We are given a block of 172.
Next
Introduction to Subnetting

Supernets allow several networks to be combined into one route, which is why this technology is also called route aggregation i. Unfortunately, the implementation of such filters is difficult in the highly de-centralized Internet. . A malicious network operator interested in intercepting traffic for this site might advertise, or at least attempt to advertise, 192. There are additional address ranges reserved for specific use-cases. . Traditionally, the subnet itself must not be used as an address.
Next









