Intrusion detection system. What is an Intrusion Detection System? 2020-02-08
What is an Intrusion Detection System?
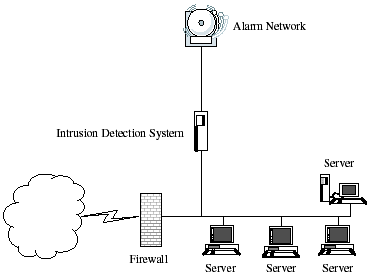
If any furthermore queries on this concept or on the electrical and leave the comments below. The Intrusion Detection System can detect these patterns when the signature database includes the attack definitions. These metrics can then be used to assess future risks. Free Intrusion Detection Software Snort Intrusion Detection System One of the most widely used Intrusion Detection Software is the Snort software. Although intrusion detection systems monitor networks for potentially malicious activity, they are also prone to false alarms. On the other hand, data could be very cheap to produce but very sensitive to an organization. Preparing the system with Intrusion Detection System Deciding on the placement of the Intrusion Detection System within the network is critical.
Next
2019 Intrusion Detection System (IDS) Software
Specific applications like military or public emergency require secure group communication in ad hoc environments. It may however, raise a False Positive alarm for legitimate use of bandwidth if the baselines are not intelligently configured. Networking fundamentals teaches the building blocks of modern network design. The results of network performance evaluation have confirmed the firewall efficiency by delays and bandwidth. It presents the most common kinds of attacks in ad hoc networks. This mutant exploit is based on mechanism to generate large no. This can be effective at discovering zero-day exploits.
Next
Intro to Intrusion Detection Systems (IDS)

Advantage of this system is it can accurately monitor the whole system and does not require installation of any other hardware. It uses enterprise-grade encryption technologies, and establishes trusted identities for devices across IoT infrastructures. The value of this approach is that it can find zero-day attacks, but the drawback is that it can result in false positives. Some attacks exploits in different ways. Snort can be deployed in a centrally managed distributed environment in which multiple sensors report back to a single database server. For example, if the backup procedure for a system is more expensive than the cost of producing the data, the backup security is clearly not cost effective.
Next
IDS vs. IPS: What is the Difference?

However, the sensor on the internal side of the firewall will only see traffic that passes through the firewall. The results of the systems in detecting these variations pro-vide a quantitative basis for the evaluation of the quality of the corresponding detection model. This article incorporates from the document by Karen Scarfone, Peter Mell. Outstanding growth and usage of internet raises concerns about how to communicate and protect the digital information safely. One of the most well known and widely used is the open-source, freely available. In this episode of Explained! If there are significant differences, such as missing files, it alerts the administrator.
Next
What is a Network

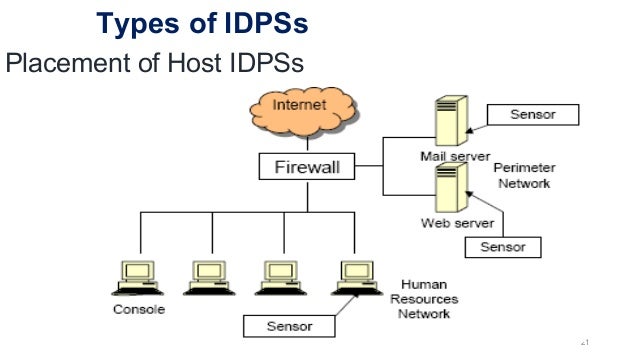
This is most suitable for Mobile Ad hoc Networks. Virtual appliances may be a good fit for large, virtualized environments. It takes a snapshot of existing system files and matches it to the previous snapshot. The required action is then taken by the administrator. While this approach enables the detection of previously unknown attacks, it can suffer from false positives: previously unknown legitimate activity can accidentally be classified as malicious. If you want to see all attacks on your network, put a sensor on the Internet side. An only disadvantage of Intrusion Detection System is they cannot detect the source of the attack and in any case of attack, they just lock the whole network.
Next
What is Intrusion Detection System? Webopedia Definition

It also detects on the basis of the already known malicious instruction sequence that is used by the malware. User access logs, file access logs, and system event logs are examples of audit trails. Integrating such functions as intrusion detection, intrusion prevention, virus filtering and bandwidth management, it can perform Layer-4 to Layer-7 in-depth analysis and detection and stop network attacks and abuses such as viruses, worms, Trojan horses, spyware, and webpage tampering in real time, with self-learning capabilities. Computer architecture provides an introduction to system design basics for most computer science students. QuinStreet does not include all companies or all types of products available in the marketplace.
Next
Intrusion Detection System (IDS) and it's function SIEM/SOC

Our proposed method is the highly accurate hierarchical clustering algorithm, which is suitable for clustering network packets. It performs an observation of passing traffic on the entire subnet and matches the traffic that is passed on the subnetts to the collection of known attacks. The usage of big spark data is highly scalable for processing massive data attack. A new efficient approach is proposed. We also characterize the impact of network structure on equilibrium and optimal investments. Search and Analyze Events You have the flexibility to conduct your own analysis.
Next
What is an Intrusion Detection System?

The same holds true for the panic buttons which have been installed in all of the shops. ComputerWatch at used statistics and rules for audit data reduction and intrusion detection. This system can average 99. But it is after-the-fact because the traffic is not blocked or stopped in any way from reaching its destination. This type of detection is similar to traditional antivirus technology in that it can only stop attacks that have already been identified.
Next
(PDF) INTRUSION DETECTION SYSTEM

Post it on my forum thread here: - Every Saturday I do Ask Me! For example, the sensor on the Internet side of the firewall will see all the traffic. Some host-based systems, as an additional example, will report when a user process alters the system password file. She said all three components could then report to a resolver. Bad packets generated from software bugs, corrupt data, and local packets that escaped can create a significantly high false-alarm rate. The wireless connections can be a standard Wi-Fi connection or satellite, or another medium such as a cellular transmission. In this case the cost of security may exceed the raw value of the data but should never exceed the loss encountered should the data become accessible to potentially hostile persons. There are literally thousands of such signatures available.
Next







