Three way handshake. TCP_3_way_handshaking 2020-02-04
What is a Three
Handshaking is a technique of communication between two entities. I believe the original idea was that there was no distinction between clients and servers. It doesn't seem to be recognized in capture filter box. This value represents the bytes that have not been read by the process. Undeterred, he took it upon himself to get to the bottom of the issue. The Three-way handshake begins with the initiator sending a with the control bit flag set.
Next
TCP

The one used was always the first one. In addition, learn how to reduce the threat of tunneling, a method hackers use to circumvent network security. Even when it does occur, it involves four packets being sent, which is more than the three packets required by the traditional 3-way handshake; ultimately only the possibility of being slightly faster to set up in terms of overall time at the cost of less overall efficiency requires 33% more packets to be transmitted. Before the sending device and the receiving device start the exchange of data, both devices need to be synchronized. From the application layer,the information is transferred to the transport layer where our topic comes into picture. ScienceDirect ® is a registered trademark of Elsevier B. The acknowledgment number is set to one more than the received sequence number i.
Next
What is a Three

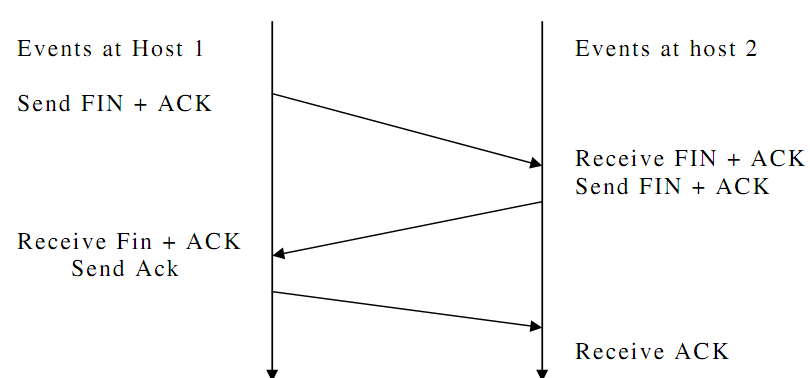
The standard process takes place as follows: 1. Fudges on kludges which when combined, produce an acceptable result. The reason I thought to direct it elsewhere is because you are now asking a different question. References- This article is contributed by Vivek Reddy. But before we can understand what an initial sequence number is, we need to understand concept of sequence numbers in general. This exchange is known as Three-way handshake.
Next
TCP three

The following are messages in the connection setup procedure. A+1, and the sequence number that the server chooses for the packet is another random number, B. This way server tells that it is ready to accept the packet with the next sequence number from the client. Each side acknowledges each other's sequence number by incrementing it: this is the acknowledgement number. The server processes listening for the clients are in Passive Open mode.
Next
Three Way Handshake: Networking & TCP/IP Tutorial. TCP/IP Explained .

Break down the handshake into what it is really doing. Note that the acknowledgment is cumulative. There must be a queue that cannot be queued and will overflow. Both knew the other's ports in a bidirectional manner, and either could start the conversation. Fudges on kludges which when combined, produce an acceptable result. There's actually a third kind of message, but we'll get to that in a moment.
Next
What is a Three
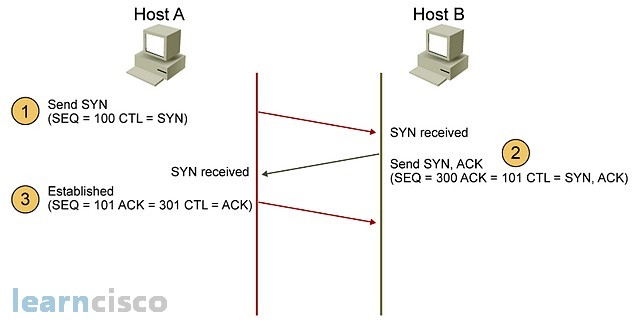
For example, when a computer communicates with another device such as a , the two devices will signal each other that they are switched on and ready to work, as well as to agree to which protocols are being used. I believe the original idea was that there was no distinction between clients and servers. The same holds true for Wireshark display filters. The syn sequence number is the initial sequence number of the server accepting the connection. The steps 1, 2 establish the connection parameter sequence number for one direction and it is acknowledged.
Next
The Three
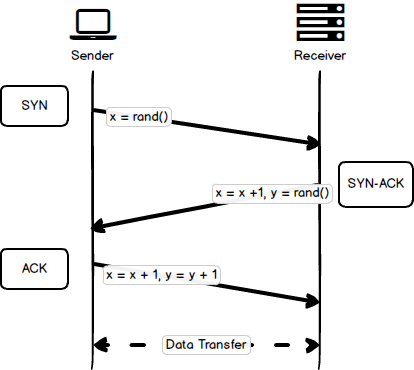
With these, a full-duplex communication is established. Effectively it ends up being a running byte count of everything that was sent. Regards Kurt You can't do this with a capture filter. This makes a total of three messages, and for this reason the connection procedure is called a three-way handshake. Why is it important to understand the three-way handshake? The development team looked at the Java source code and found that the default value of the backlog of the socket was 50 this value controls the size of the complete connection queue and will be detailed later. The 2605483509 is to inform My Computer that the previous data was received successfully. I am including the Wireshark screen shots also, to understand the concepts more clearly.
Next
TCP 3

But in practice, three steps turns out to be good enough for most purposes. But in practice, three steps turns out to be good enough for most purposes. The use of sequence and acknowledgment numbers allows both sides to detect missing or out-of-order segments. The only way to be sure that you got a packet to the other side is by getting a packet from them that, by definition, would not have been sent unless the packet you sent got through. It's priced very economically and you can read all of it in a convenient format without ads.
Next







